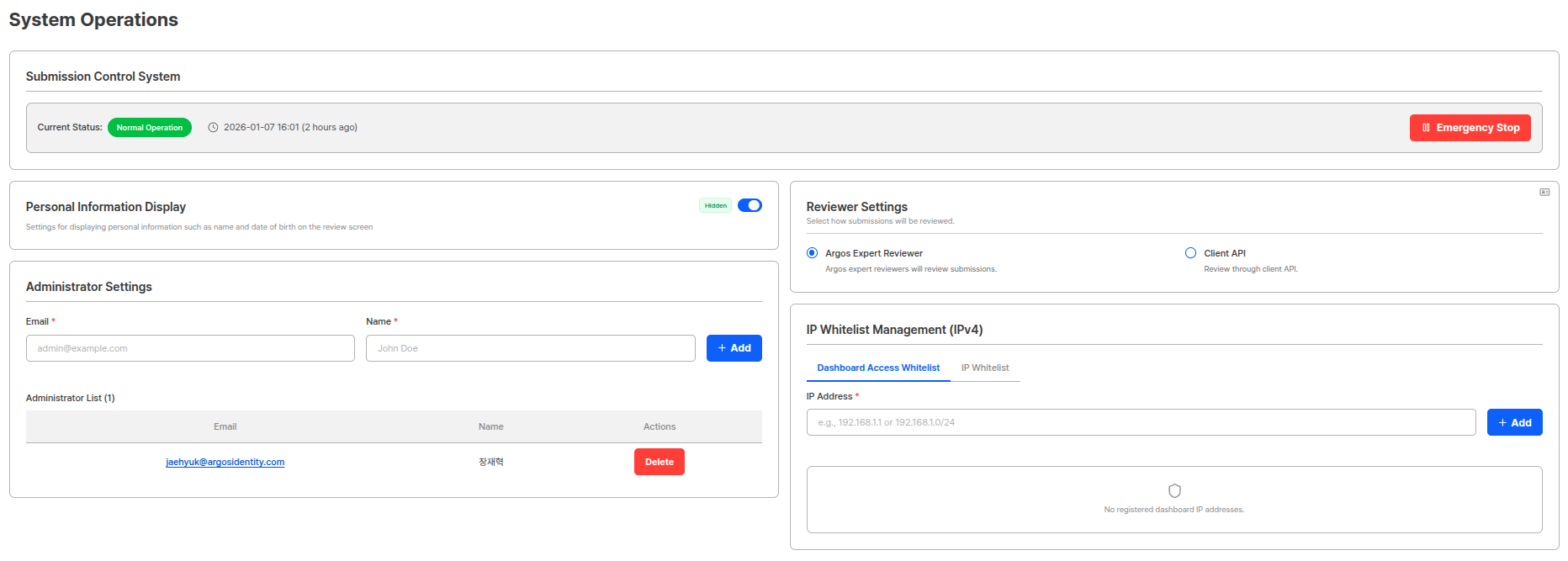
Submission Control System
You can prepare for emergency situations through the submission control system.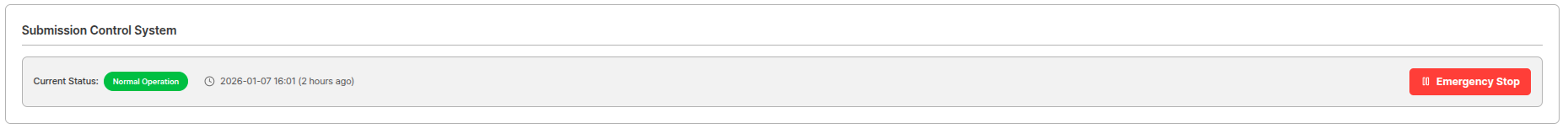
| Status | Description |
|---|---|
| Normal Operation | All eKYC processes are operating normally. |
| Emergency Stop | eKYC submissions are stopped. (eKYC submissions via Liveform, submissions via Post/submission) |
Privacy Display Settings
You can configure whether to display personal information in the dashboard.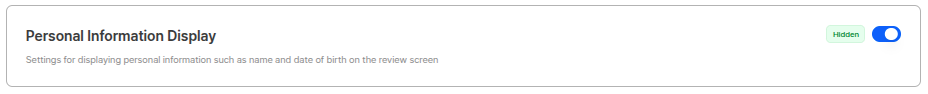
- ID Image: Submitted ID images are blurred.
- ID Number: ID numbers are masked.
- Document Number: Document numbers are masked.
Privacy Protection UsageWhen there are multiple administrators with dashboard access permissions, you can activate the privacy display function to hide sensitive information on the screen. This helps comply with privacy protection laws and strengthen internal security.
Administrator Settings
You can manage access permissions by project.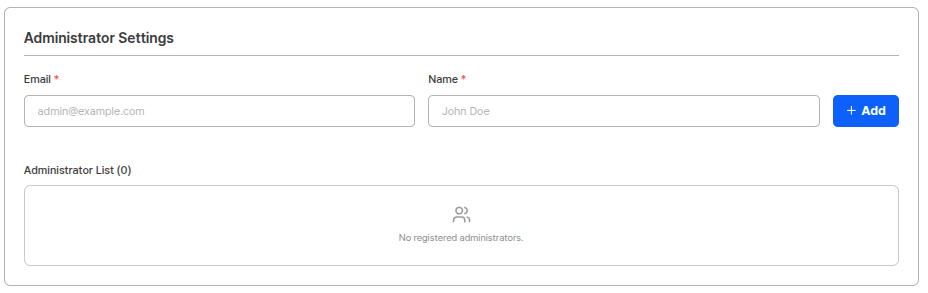
- Add Administrator: Register the email of an administrator to grant project access permissions.
- Remove Administrator: Remove access permissions of registered administrators.
- View Login Records: Click on an administrator account to view login records for that account.
Administrator Permission ManagementCurrently, only addition/removal of project access permissions is available. Detailed permission management functions will be added in the future.
Reviewer Settings
You can configure who will review submissions that require manual review.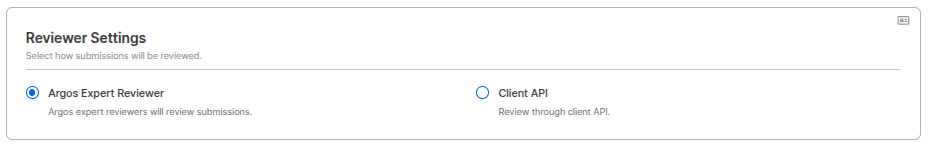
- ARGOS Professional Reviewer: ARGOS reviewers directly review.
(Reviews submissions for pending items within a maximum of 24 hours. For faster review processing, please contact sales.) - Client API: The customer becomes the review entity and reviews directly.
You can directly modify kycStatus for pending items in the dashboard, and use the Review API for faster processing.
Review is needed when the submission score falls below the ARGOS Score threshold value, resulting in a pending item.
IP Whitelist Management (IPv4)
You can restrict dashboard viewing and API access to only specified IP addresses.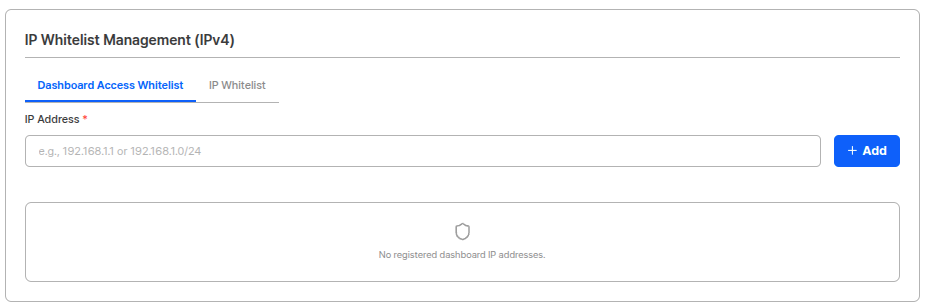
- Dashboard Access: Dashboard login is only possible from registered IPs.
- API Access: API calls are only possible from registered IPs.
- Activate the IP whitelist function.
- Enter IPv4 addresses to allow. (One per line)
- Click the save button to apply settings.
IP Whitelist UsageSetting up an IP whitelist can block unauthorized access from outside and strengthen security. It is recommended to set this up when handling sensitive data including customer information.