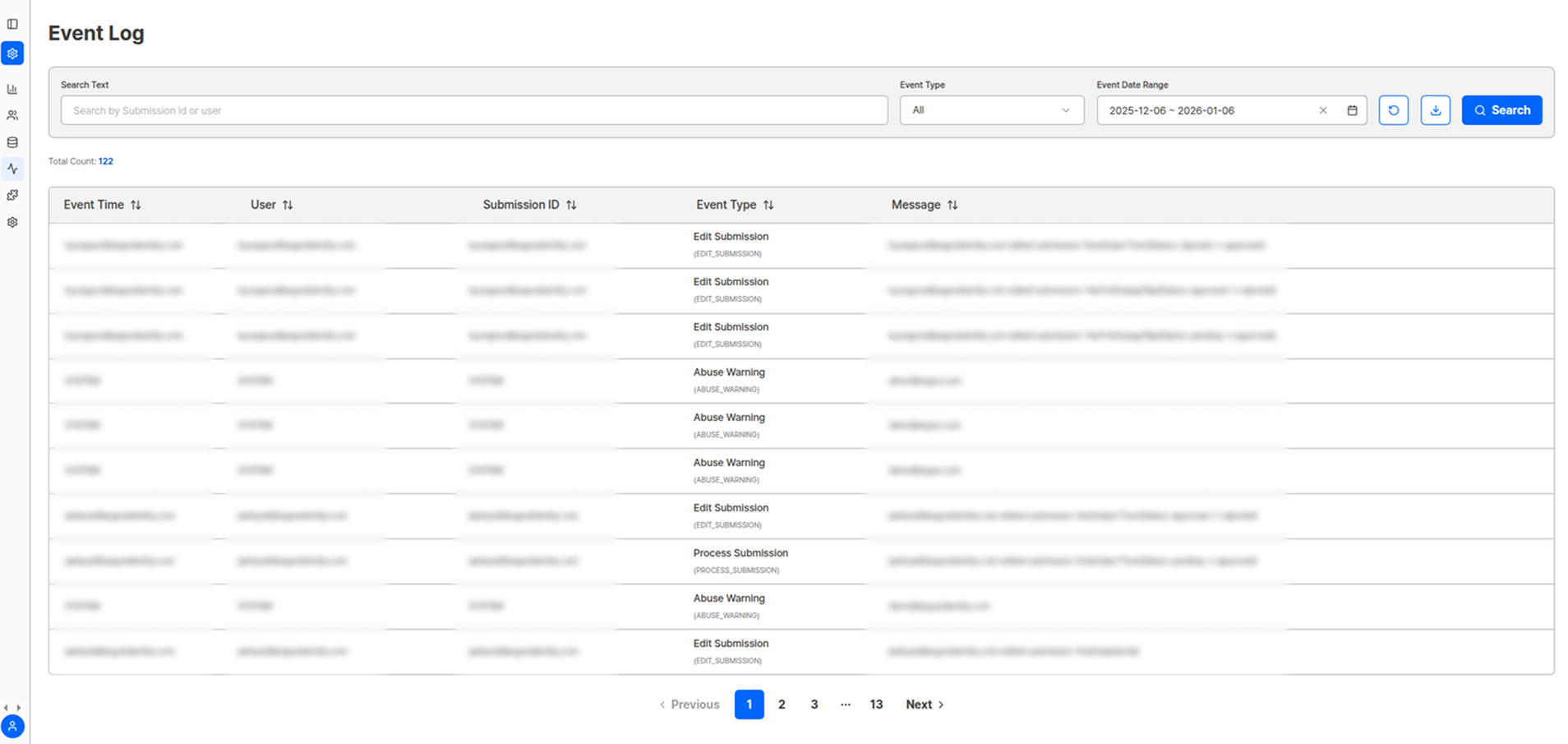
Search and Filter Options
| Option | Description |
|---|---|
| Specific Person Name | Track event logs for individual users |
| Submission ID | View complete event history for a specific submission |
| Event Type | Filter by desired event type |
| Date Range | Query only events that occurred within a specific period |
Trackable Event Types
| Event Category | Included Content | Purpose |
|---|---|---|
| Submission Process | Submission start, step-by-step progress, completion/abandonment | Analyze user behavior patterns |
| Authentication Results | Approval, rejection, pending status changes | Track decision process |
| Administrator Activity | Account addition/deletion, permission changes | Security and access management |
| Data Management | Submission deletion, information modification | Ensure data integrity |
| System Events | Errors, warnings, system notifications | System monitoring |
How to Use Event Logs
Troubleshooting
Analyze causes of submission failures and derive solutions.
Security Audit
Review administrator activity and data access history.
User Support
Understand the exact situation when users inquire.
Process Improvement
Improve UX by analyzing event patterns.
Event logs can also be used as important evidence to meet audit requirements for regulatory compliance.
Administrator Permission Logs
All activities related to administrator permissions within the project are recorded:- New administrator account addition
- Existing administrator account deletion
- Permission level changes
- Access permission modifications
Submission Deletion Logs
Records of deleted submissions are maintained for data protection and tracking:| Record Item | Description |
|---|---|
| Deletion Executor Information | Who executed the deletion |
| Deletion Time and Date | When it was deleted |
| Deletion Reason | Reason for deletion (optional) |
| Deleted Submission Basic Information | Which submission was deleted |