The scope of displayed information and modifiable items may vary according to User Policy Settings for each project.
Submission List
You can check the status of all submissions recorded within the project. Query in detail by search criteria, date range, nationality, and submission status.Available Information
The following information can be viewed in the submission list:| Item | Description |
|---|---|
| Submission Time | Time when submission occurred |
| Submission Unique ID | Unique identifier for each submission |
| Email Address | Submitter email |
| Name | Submitter name |
| Date of Birth | Submitter date of birth |
| Nationality | Based on issuing country |
| AML Information | AML search results per submission |
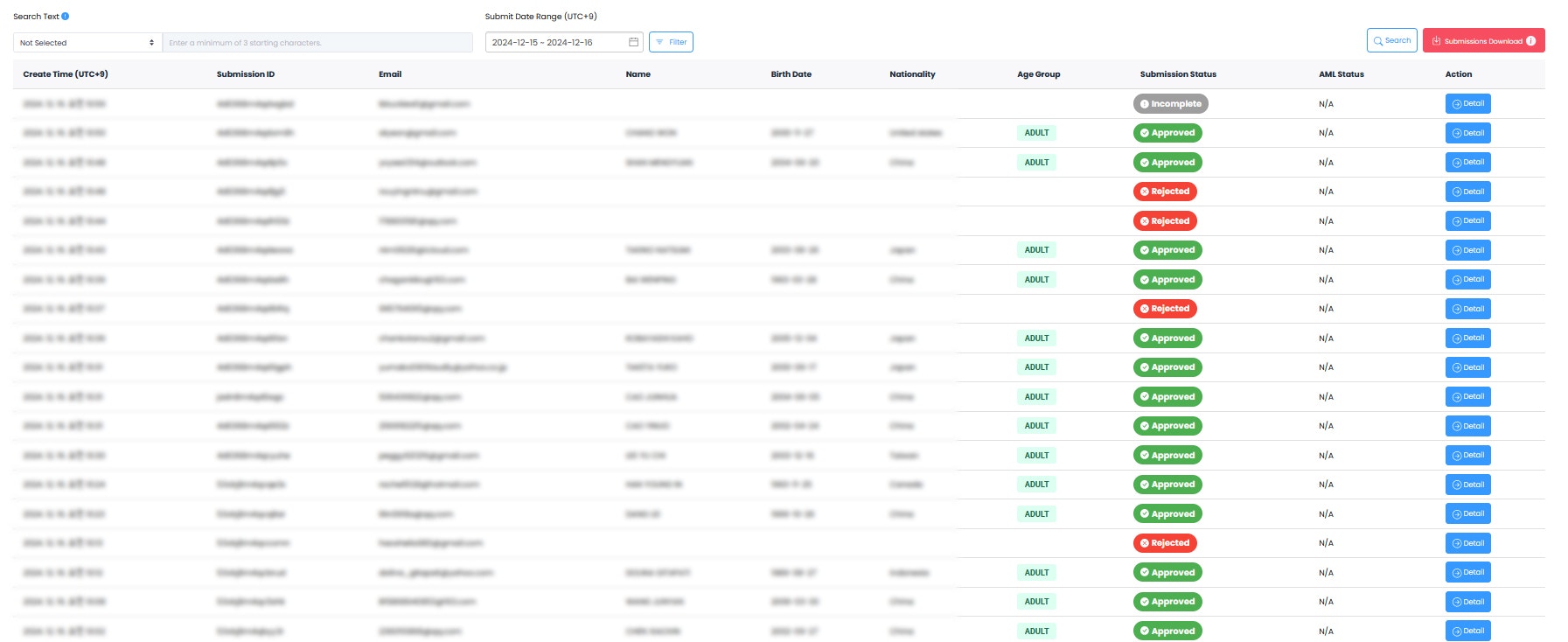
Search and Filter Features
Use the following features for efficient submission management:- Date Range Setting: Query submissions for specific periods
- Status Filter: Filter by Approved/Rejected/Pending/Incomplete status
- Nationality Query: Filter submissions by specific country
- Keyword Search: Search by name, email, etc.
- AML Result Classification: Classification by AML search results
Submission Detail View
Click the Detail View button on the right side of each submission to view and modify all recorded information.Collected information fields may vary according to authentication options set for each project.
Submission Management Features

Delete Submission
Delete a specific submission for that user. Detailed data is removed upon deletion and cannot be restored.
Generate PDF
Download submission information as a PDF document.
Send Webhook
Send submission data to external systems via webhook functionality.
Deletion records themselves can be viewed on the Event Log Page.
Top Information in Submission Detail View
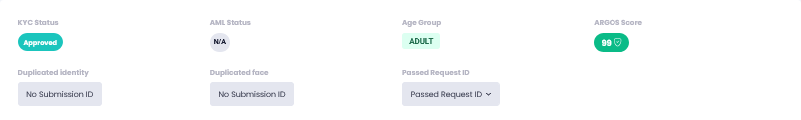
The image above shows from eKYC Result to Other Information Fields.
eKYC Result
- Approved
- Rejected
- Pending
- Incomplete
When normal authentication documents and selfie have all been verified
AML Result
| Result | Description |
|---|---|
| N/A | No AML results available for reference (mainly seen when dropped during liveform) |
| No Match | No person of interest information based on submitted materials |
| Red Flag | Risk/concern person information exists based on name/nationality/date of birth |
Other Information Fields
Age Group
Age Group
Categorized as Adult/Teen/Early Teens/Minor. Not displayed in Incomplete status.
ARGOS Identity Score
ARGOS Identity Score
Score calculated by AI based on submitted information, photos, and AML results.
Duplicate Identity Information
Duplicate Identity Information
Displays other submissions within the same project matching this submitter’s information.
Duplicate Face
Duplicate Face
Displays other submissions within the same project matching this submitter’s facial information.
Pre-verification List
Pre-verification List
Displayed when IP addresses identified as forgery or commercial purpose are filtered through Proxy & VPN option activation.
User Information
View information from when submitter executed this submission: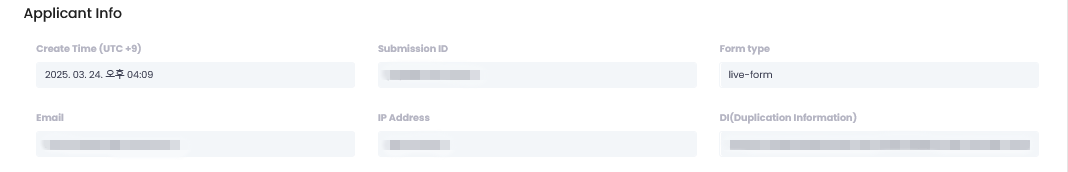
| Field | Description |
|---|---|
| Submission Time (UTC+9) | Submission occurrence time based on Korea server time |
| Submission ID | Unique ID for each submission |
| Service Type | Submission format |
| Email address mapped to this submission | |
| IP Address | IP connected at submission time |
| DI (Duplicate Information) | Unique encrypted value generated upon identity verification approval |
DI Value Generation ConditionsDI value is generated when name, date of birth, gender, nationality, etc. are all provided. If the same identity is verified through ARGOS Identity service, the existing DI value is maintained even when authenticating in different projects.
Metadata
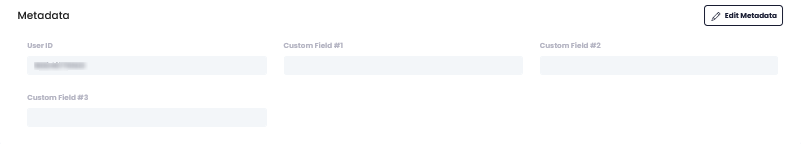
| Field | Description |
|---|---|
| User ID | Unique user ID |
| Custom Field #1 ~ #3 | Values entered when additional input is requested |
Memo Feature
ID Document Information
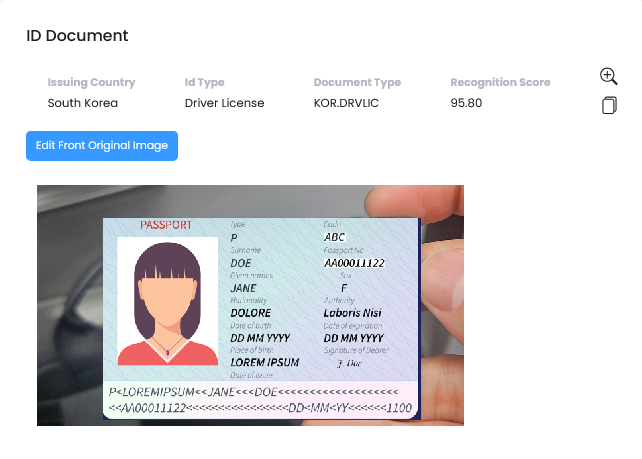
| Field | Description |
|---|---|
| Issuing Country | Issuing country of submitted ID (may differ from nationality) |
| ID Type | Type of ID selected by submitter |
| Document Type | Issuing country & ID type |
| Recognition Score | Recognition score collected from ID capture |
- 🔍 Magnifying Glass: Zoom in/out
- 🔄 Edit: Rotate, flip horizontal, reset to original
- ✂️ Image Crop: Auto-zoom to ID center
- 🖌️ Masking: Apply masking directly if needed
Submission Information
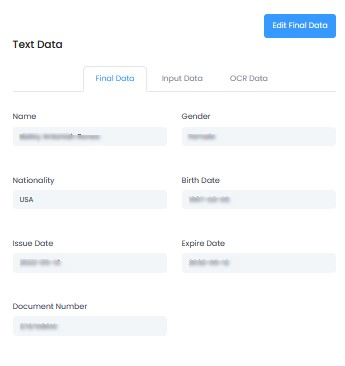
| Data Type | Description |
|---|---|
| OCR Data | ID information results initially detected by AI camera |
| Input Data | Values when user modified OCR data |
| Final Data | Final data modified based on OCR data |
Selfie Information

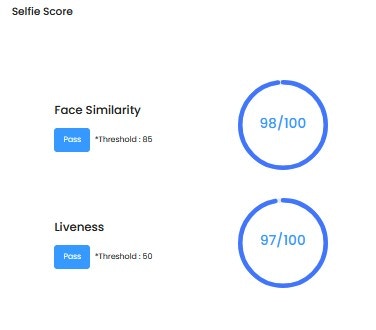
| Score Type | Description |
|---|---|
| Face Similarity | Passes when above set threshold out of 100 points |
| Liveness | Passes when above set threshold out of 100 points |
Address Information
Displays Geo-Location information based on IP address at submission time.Address information is only displayed when the related feature is activated.
User Data Download
API Call Limits
| Limit Type | Quota | Description |
|---|---|---|
| Max Requests per Second (QPS) | 5,000 requests | Maximum API requests processable in 1 second |
| Max Requests per Day (QPD) | 100,000 requests | Total API requests allowed in 24 hours |
Pre-verification List
When Proxy & VPN Detection option is activated, related details can be checked for each submission. Pre-blocks submissions through specific IP ranges or Private networks where forgery/alteration frequently occurs.Feature Activation MethodActivate the ‘Proxy & VPN Detection’ option in Settings > Fraud Prevention menu.
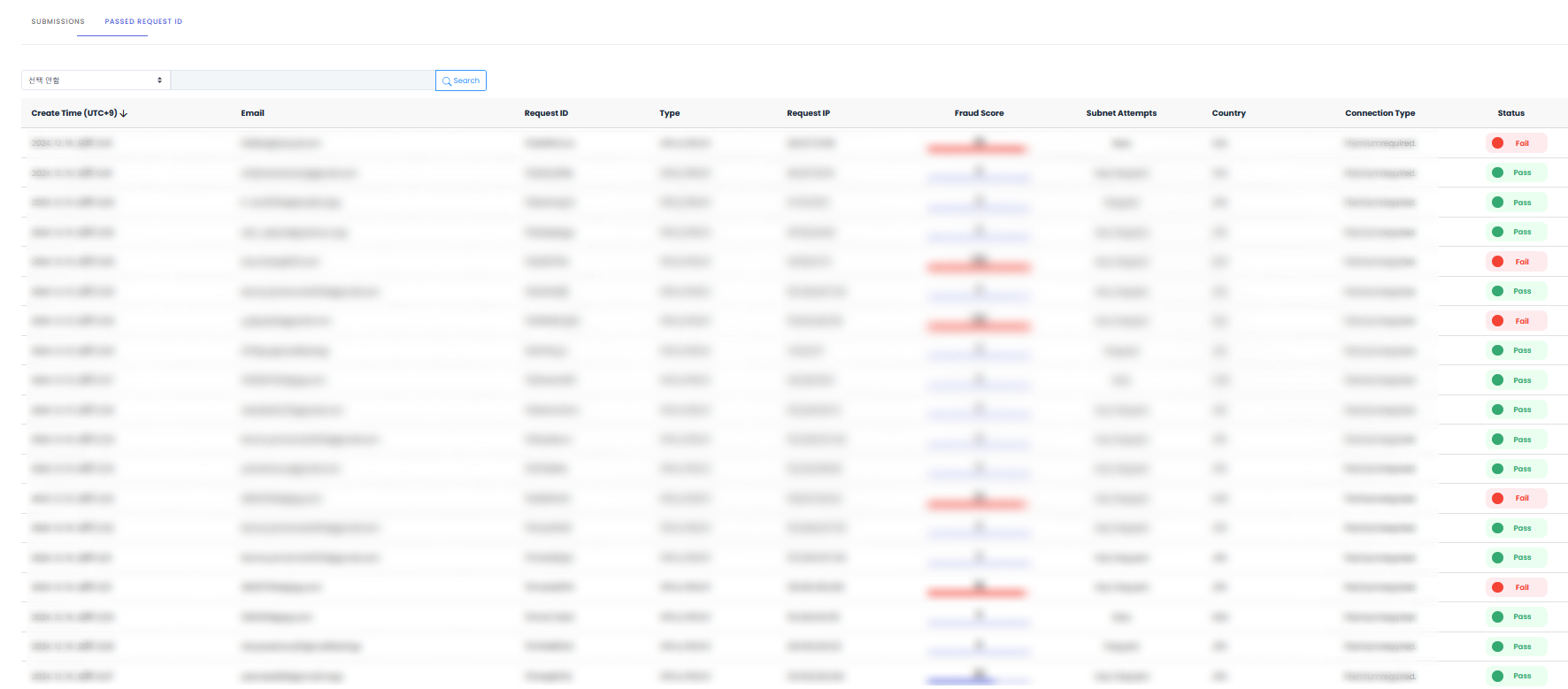
Available Information
| Item | Description |
|---|---|
| Submission Time | Submission attempt time |
| Email Address | Submitter email |
| Request ID | Unique request identifier |
| Detection Type | Proxy, VPN, TOR, etc. |
| Request IP | Submission attempt IP |
| Risk Score | IP-based risk score |
| Service Attempt | Whether service access was attempted |
| Country | IP-based country information |
| Connection Type | Connection method |
| Final Status | Block/Allow result |
The pre-verification list page is view-only and cannot be modified, unlike submission list detail pages.
Benefits of Proxy & VPN Detection
Enhanced Security
Pre-block risky IP ranges
Integrity Protection
Protect service by pre-detecting forgery/alteration attempts
Abuse Prevention
Prevent commercial purpose abuse
Access Restriction
Enable regional access restriction policies
Response by Detection Type
| Detection Type | Risk Level | Recommended Response |
|---|---|---|
| Proxy | Medium | Apply additional verification procedures |
| VPN | Medium | Apply additional verification procedures |
| Commercial VPN | High | Immediate block or enhanced verification |
| Hosting Provider | High | Automatic rejection processing |
Pre-verification Detail View
Click the Status button for each pre-verification case to view detailed Proxy & VPN detection information.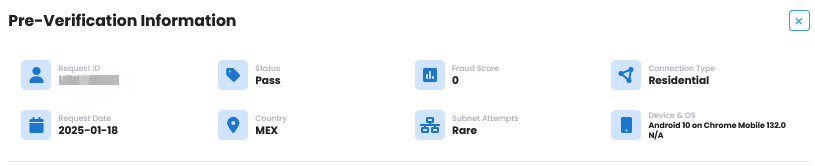
Pre-verification Information
| Field | Description |
|---|---|
| Request ID | Unique request value generated during identity verification attempt |
| Status | Pass/fail based on IP and related information |
| Risk Score | Score quantified from IP and related information |
| Connection Type | Residential/Mobile/Data Center |
| Request Date | Date of submission attempt |
| Country | IP-based country information |
| Subnet Attempt | Subnet submission attempt frequency (First occurrence/Rare/Very frequent) |
| Device and OS | Submission upload environment information |
IP Anonymization Status
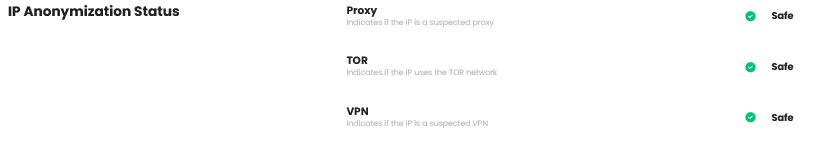
| Item | Description |
|---|---|
| Proxy | Whether IP is suspected to be a proxy |
| TOR | Whether IP is using TOR network |
| VPN | Whether IP is suspected to be a VPN |
IP Abuse Records
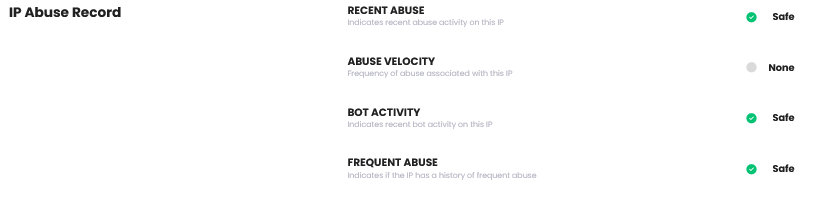
| Item | Description |
|---|---|
| Recent Abuse | Whether recent abuse records exist for this IP |
| Abuse Velocity | Abuse frequency related to this IP |
| Bot Activity | Whether recent bot activity exists for this IP |
| Frequent Abuse | Whether frequent abuse history exists for this IP |
Additional Information
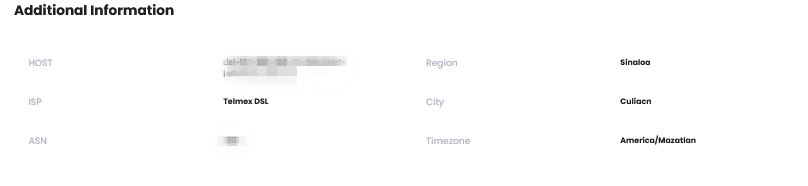
| Item | Description |
|---|---|
| Host | Host information |
| Internet Service Provider | ISP information |
| Autonomous System Number (ASN) | Unique autonomous system number |
| Region | IP-based region information |
| City/District | IP-based detailed region information |
| Timezone | IP-based timezone information |
Risk Score Interpretation Guide
| Score Range | Risk Level | Recommended Action |
|---|---|---|
| 0-30 | Low | Normal processing |
| 31-60 | Medium | Additional monitoring |
| 61-80 | High | Enhanced verification procedures |
| 81-100 | Very High | Immediate block recommended |